AWS Security Best Practices
AWS provides its users with a wide variety of managed security services, as well as security guidelines and patterns. When followed, these services help ensure that your business can meet any regulatory requirement. In fact, security forms one of the six pillars of the “AWS Well-Architected Framework”. This framework is designed to help compare your infrastructure against industry best practices and identify any weaknesses or areas for improvement.
With cloud vulnerabilities increasing by 150% over the last five years (and continuing to grow at a rapid pace) it's clear that securing your cloud resources is an ever-growing challenge. By following some of the best practices outlined in this article, you can ensure the safety of your infrastructure and data while maintaining operational efficiency and efficacy. Below is an executive summary of some of the key principles we will be covering in this article.
Executive Summary
| Principle | Key Solutions |
| Security Driven Development | Integrate security into every development phase |
| Access Control | Root Access, Password Policies, etc |
| Least Privilege | SCP, IAM |
| Infrastructure As Code | Reliable repeatable secure infrastructure |
| Continuous Monitoring | Range of managed solutions |
| Protect Data In Transit | SSL, VPN |
| Protect Data At Rest | Encryption |
Security Driven Development
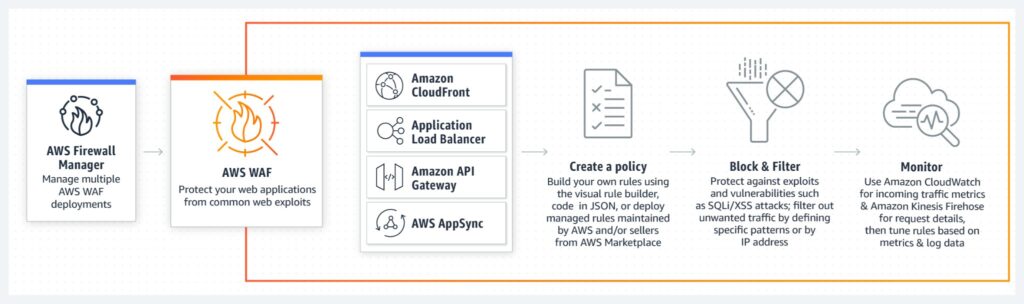
When using AWS managed services, always take time to review the different security features on offer. For example, when using AWS API Gateway, consider using WAF to protect your API endpoints from common exploits, such as SQL injection or cross-site scripting (XSS) attacks.
When using services such as Lambda or Fargate, use frameworks and guidelines such as those provided by OWASP (Open Web Application Security Project) that secure your code base from common exploits.
Another useful utility is AWS Codeguru. This automates your code reviewing processes by using Machine Learning to identify critical issues, vulnerabilities, or bugs not identified during the manual code review, as well as assisting subsequent remediation.
AWS Web Application Firewall protects your applications from common exploits (source)
Access Control
With attacks increasing in frequency and sophistication, it can be easy to forget the more basic steps that help secure your AWS account. A root user is created by default when setting up an AWS account. This user has unrestricted access to all AWS services and should therefore never be used for day-to-day tasks.
After creating a new account, you should always enable Multi-Factor-Authentication (MFA) for the root user, change its password and delete any associated access keys. For other users, you should always implement strong password policies.
A study carried out by Netskope in 2021 shows many users favor convenience over security, a dangerous compromise in this day and age. As a result, Netskope suggest several best practices, including enforcing a minumum password length of 14 characters and requiring any new password to be different from the previous 23.

|
Platform
|
Provisioning Automation |
Security Management |
Cost Management |
Regulatory Compliance |
Powered by Artificial Intelligence |
Native Hybrid Cloud Support
|
|---|---|---|---|---|---|---|
|
AWS Native Tools |
✔
|
✔
|
✔
|
|||
|
CoreStack
|
✔
|
✔
|
✔
|
✔
|
✔
|
✔
|
Least Privilege
The principle of least privilege is designed to reduce the impact of users, either deliberately or accidentally, misusing an information system to which they have legitimate access. This is done by restricting access-rights and permissions to the bare minimum.
With AWS, you can implement this principle by using the IAM (Identity Access Management) service to define roles and groups. Users and systems with specific requirements can be assigned a corresponding role. The role in turn is associated with a specifically restricted set of capabilities, safeguarding the system from potential misuse.
By default, users and systems (apart from root) start with no permissions at all. This means access to any resource must be explicitly allowed. Take for example an AWS Lambda, which only requires access to read and write from a specific S3 bucket. It should not have access to delete items, nor should it have access to any other bucket. Similarly, it should not have access to any other services except S3. You can achieve this using IAM roles and policies, such as the example below:
MyDemoPolicy:
Type: AWS::IAM::ManagedPolicy
Properties:
ManagedPolicyName: MyDemoPolicy
PolicyDocument:
Version: 2021-10-17
Statement:
- Effect: Allow
Action:
- s3:GetObject
- s3:PutObject
Resource:
- "arn:aws:s3:::my-demo-bucket"
Roles: [ !Ref MyDemoRole ]
This attaches a policy to MyDemoRole. Any user or service (a specific lambda function, for example) assigned this role can read (GetObject) and write (PutObject) to the specified resource.
The process of designing the perfect architecture is far from trivial, often involving multiple teams collaborating on a single architectural diagram that represents the entire solution. Administrators then use this blueprint to create, configure and deploy the various system components. With a complex solution, this is time consuming and laborious. Each time the blueprint is manually implemented, there is a risk of human error introducing a mistake which can result in operational challenges or increased security risks.
Infrastructure As Code
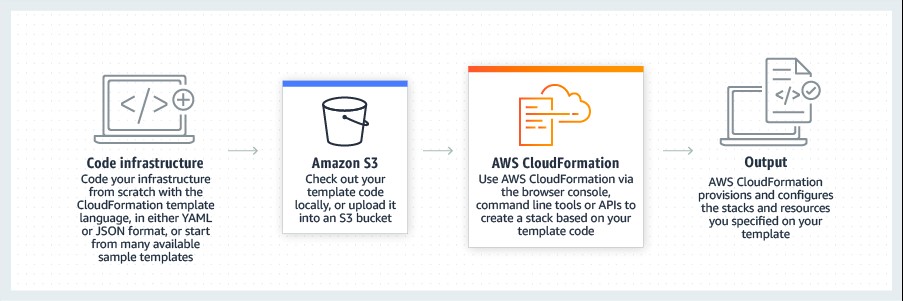
CloudFormation, the AWS Infrastructure as Code service, is a good solution to this problem. By defining an entire architecture within error-checked and well maintained code, human introduced flaws can be minimized. This also enables rapid and consistent deployments across different environments. When stored into a version control system, all infrastructure changes can be recorded, versioned and even reverted if necessary.
AWS CloudFormation lets you provision and manage all of your resources as code (source)
Continuous Monitoring
AWS provides several services for tracking activity withing your environment. The core services currently available are CloudTrail, GuardDuty, CloudWatch, and Security Hub:
- CloudTrail is a governance-driven tool, used to audit all actions carried out by users, roles, and services in your AWS account
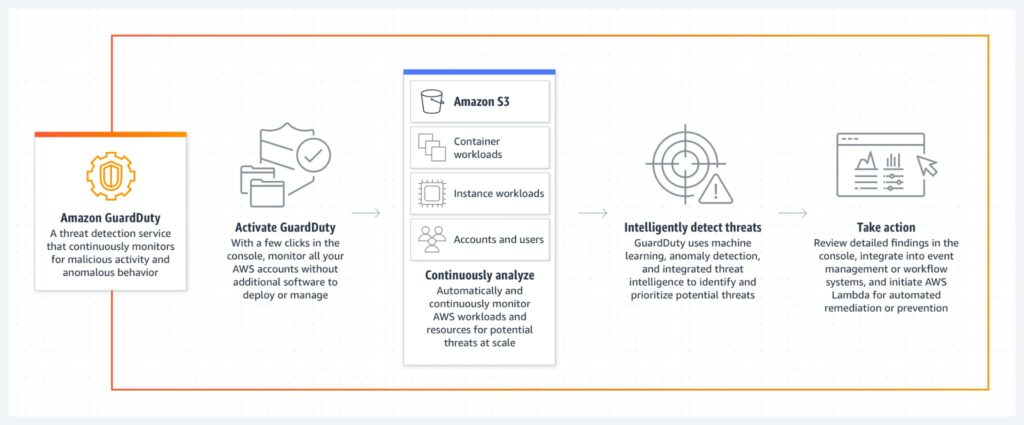
- GuardDuty uses a machine learning technique, known as anomaly detection, to analyze records and events across various AWS data sources to identify suspicious or unusual activity
- CloudWatch allows you to collect, access and correlate all data across all resources, both on AWS and on-prem. This provides users with complete system-wide visibility
- Security Hub is a service that provides a single place to view all continuous monitoring activities. It also integrates with services like WAF and VPC FlowLogs and automatically aggregates any security findings
Whenever integrating a new service into your solution, investigate what logging configurations are available to you.
Guard Duty delivers AI-driven security analysis (source)
Protect Data In Transit
The importance of protecting data in transit has not changed with the emergence of cloud computing. AWS takes care of encrypting all internal traffic and provides comprehensive solutions to ensure that this is applied regardless of architecture.
Here are some AWS services that assist with the protection of data in transit:
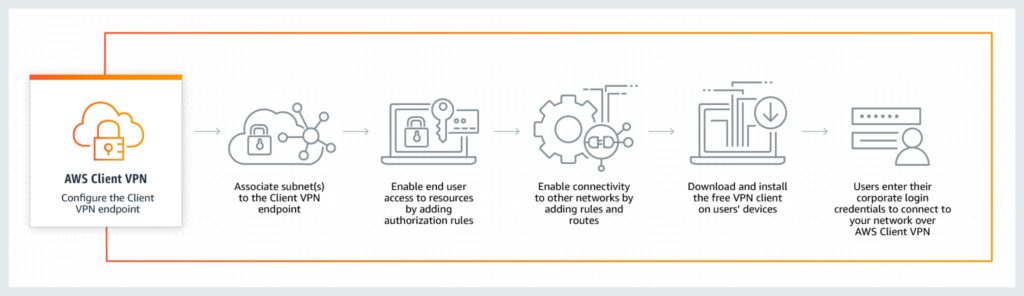
- AWS VPN is a managed VPN (Virtual Private Network) solution that provides the required level of secrecy and integrity to your network traffic as it traverses between locations
- AWS Certificate Manager (ACM) lets you create Transport Layer Security (TLS) certificates for use with AWS services and internally connected resources
- CloudFront, API Gateway and Load Balancers can all be configured to enforce HTTPS connections
Secure your remote access to resources within your network with AWS VPN (source).
Protect Data At Rest
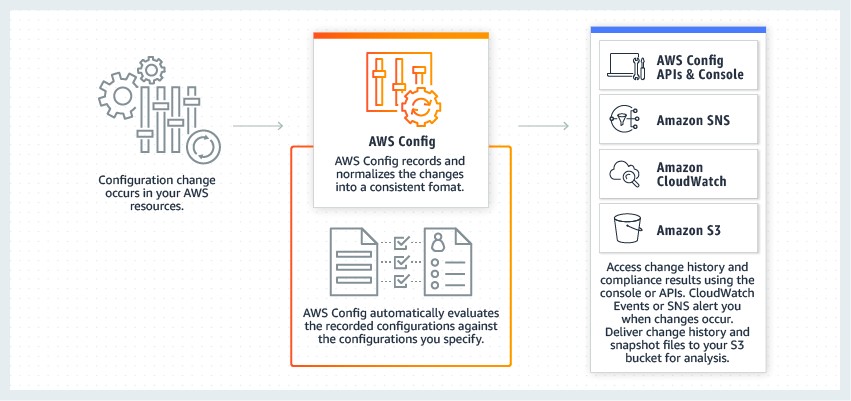
Similarly, AWS has not ignored the importance of protecting data at rest. Services such as S3 and DynamoDB integrate with the AWS Key Management Service (KMS), making the creation, management, and usage of cryptographic keys simple. Furthermore, the AWS Config service can be used to monitor the encryption configuration of your various storage-based services, such as RDS, S3, and DynamoDB.
Continuously monitor changes to all resources with AWS Config (source)

|
Platform
|
Provisioning Automation |
Security Management |
Cost Management |
Regulatory Compliance |
Powered by Artificial Intelligence |
Native Hybrid Cloud Support
|
|---|---|---|---|---|---|---|
|
AWS Native Tools |
✔
|
✔
|
✔
|
|||
|
CoreStack
|
✔
|
✔
|
✔
|
✔
|
✔
|
✔
|
Conclusion
The best practices we’ve discussed above (and the tools that support them) provide a good grounding to improve, monitor and maintain security across all aspects of your infrastructure. Building a team and a process around these guidelines will help your organization get its policies and practices right, in as few iterations as possible. If you'd like to learn more, read some of our other security best practice articles below:
Chapter 1 – AWS Security Group Best Practices
Learn the most important AWS Security Group best practices and follow step-by-step instructions and examples to configure them.
Chapter 2 – S3 Security
Learn the AWS S3 security principles of least privilege, access monitoring, encryption, and more, to protect against misconfiguration and data leakage.
Chapter 3 – AWS NACL
An introduction to AWS NACLs and their differences from Security Groups. Learn how to use AWS NACLs through practical examples and best practices
Chapter 4 – API Gateway Security
Learn how to protect your API gateway through the use of CloudWatch, X-Ray, Identity and Access Management (IAM), Cognito, and gateway security best practices
Chapter 5 – EBS Encryption
Learn about the advantages of encrypting your AWS EBS volumes and how to encrypt both new and existing volumes through step-by-step examples
Chapter 6 – AWS Parameter Store vs Secrets Manager: Detailed Comparison
Deep dive into the differences between AWS Parameter Store and AWS Secrets manager for storing secrets and configuration data through detailed examples
Chapter 7 – Amazon Inspector Essentials
Learn how to assess and improve EC2 and ECR security using Amazon Inspector. An introduction to Amazon Inspector setup, automation, risk score analysis, pricing, and integration with AWS services.
Chapter 8 – IAM Best Practices
Learn the most important AWS Identity and Access Management best practices. Learn how to grant permissions using the principle of least privilege, authentication, and access control.
Chapter 9 – Inline Policy AWS Introduction
Learn how and when to use AWS inline policies. Introduction to the difference between inline and managed policies, common use cases, risks related to inline policies, and best practices on how to use them.
Chapter 10 – Container Security in AWS
Learn how and when to use AWS inline policies. Introduction to the difference between inline and managed policies, common use cases, risks related to inline policies, and best practices on how to use them.
Chapter 11 – AWS Tagging: Best Practices
Tagging your AWS resources can help with more than just organization. Learn how to track costs, govern security, and more with these AWS tagging best practices.
More chapters coming soon!