Amazon Inspector Essentials
Amazon Inspector is a security assessment service by Amazon Web Services (AWS) that automates AWS workload vulnerability scanning. It utilizes automation to provide continuous threat detection and has no need for manual intervention. This means that known vulnerabilities can be detected quickly and this reduces your Mean Time to Remediate (MTTR). MTTR is the average length of time it takes an organization to identify and resolve security threats.
Amazon Inspector assessment enables the discovery of software vulnerabilities and any unintended network exposure for several AWS services. Inspector allows you to consolidate vulnerability solutions into a single easy-to-use dashboard. Threats are analyzed by Inspector and results are presented via an easy to interpret risk score. You can then use this to prioritize any necessary remediation.
Amazon Inspector can help you meet the compliance requirements of NIST CSF, PCI DSS as well as best practices set by NSA/CISA.
Executive summary
In this article we will review the following aspects of implementing AWS Inspector:
| Automation of Security Threats | Discover how Amazon Inspector can automate security threat detection |
| Inspector findings and Risk Score analysis | View and dissect the Inspector Findings and learn how Risk Scores are calculated |
| Pricing summary and examples | Review the pay-as-you-go pricing model AWS provides for Inspector |
| Integration with AWS services | Learn how Inspector integrates with other AWS services |
| Amazon Inspector tutorial | An introductory and practical tour of Inspector |
| Limitations of Amazon Inspector | Learn about security systems that should be implemented alongside Inspector, helping form more robust Information Security |
| Best Practices and recommendations | Review best practices for configuring and optimizing Inspector |
Improving AWS security
Automating vulnerability scanning and proactively identifying risks is an essential step for any organization wanting to harden their security defenses. In contrast to manual mechanisms, security automation simplifies threat detection, improves protection from malicious actors, and improves MTTR.
Security automation
Amazon Inspector continuously and automatically scans workloads on Amazon Elastic Compute Cloud (EC2) as well as Amazon Elastic Container Registry (ECR) container images for common vulnerabilities and exposures (CVEs).
AWS is seen as a leader in Cloud Computing, largely due to the quantity and quality of its managed services. A managed service provides its functionality without requiring the user to set up, manage or maintain the underlying infrastructure. Because of this, operational overhead and human errors are greatly reduced. Amazon Inspector is an example of just such a managed service.
When configured for automated discovery, all newly provisioned EC2 instances and container images are immediately scanned for vulnerabilities. When configured for continuous scanning, any EC2 instance that indicates it may have a new vulnerability is re-scanned. See here for details.
Inspector can be deployed to all workloads in your AWS Account with a single click, and once enabled it immediately scans all systems. The deployment can include all member accounts associated with an AWS Organization (see here). This establishes almost real-time vulnerability detection within your entire organization.
Inspector Findings and Risk Score Analysis
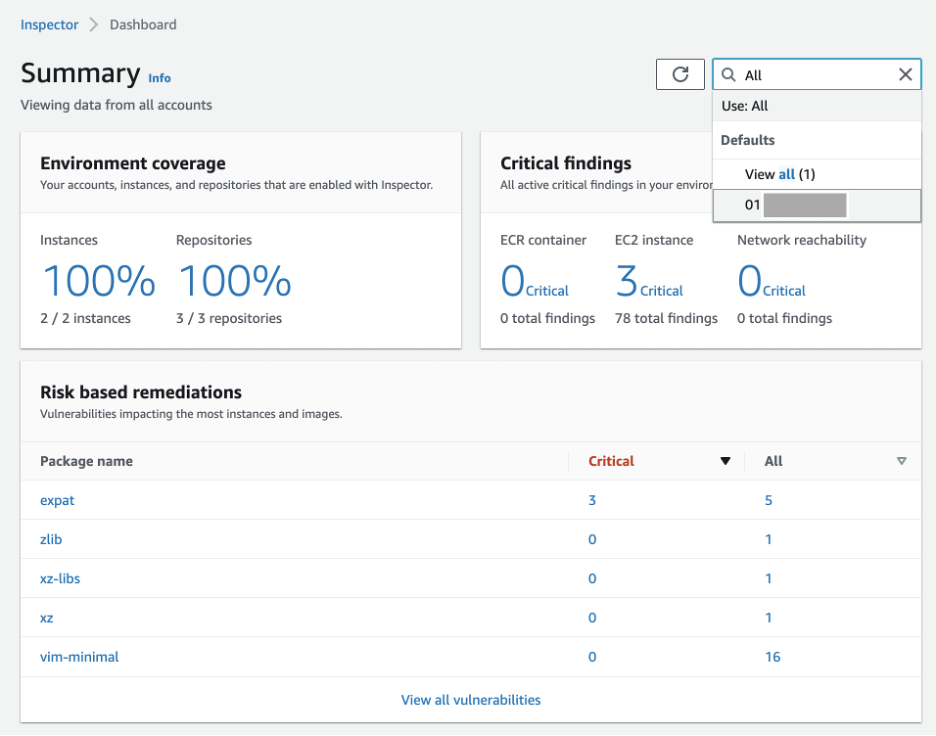
Amazon Inspector provides an intuitive dashboard that displays metrics covering EC2 instances and ECR repositories within the current AWS region. The Inspector Dashboard provides a quick way to gauge your scanning coverage and highlights any vulnerabilities that pose risk to your AWS environment.
For multi-account Inspector Organization administrators or delegated administrators, the dashboard will display information for all AWS Accounts in the AWS Organization. Results may be filtered to display information related to only a specific account if required. Creating a delegated administrator account is a recommended best practice to improve security.
Image shows Amazon Inspector Dashboard
Findings are classified by a proprietary ranking system with a score between 0.0 and 10.0. Critical vulnerabilities are assigned a higher score than those classified as low risk.
Discovered vulnerabilities are associated with real-time descriptive information via Common Vulnerabilities and Exposures (CVE) data sources. CVE is the public system that allows for the sharing of information on cybersecurity vulnerabilities and exposures – check here for more information. CVE data is correlated with AWS environmental configurations, including network reachability and AWS security policies, to determine the Inspector Risk Scores and to prioritize results.
Risk Score severity ratings are assigned to vulnerabilities as follows:
| Score | Rating |
|---|---|
| 0 | Informational |
| 0.1 – 3.9 | Low |
| 4.0 – 6.9 | Medium |
| 7.0 – 8.9 | High |
| 9.0 – 10.0 | Critical |
Table shows Amazon Inspector Risk Score Severity Ratings

|
Platform
|
Provisioning Automation |
Security Management |
Cost Management |
Regulatory Compliance |
Powered by Artificial Intelligence |
Native Hybrid Cloud Support
|
|---|---|---|---|---|---|---|
|
AWS Native Tools |
✔
|
✔
|
✔
|
|||
|
CoreStack
|
✔
|
✔
|
✔
|
✔
|
✔
|
✔
|
Pricing summary and examples
Amazon Inspector is a pay-as-you-go managed service. You pay only for the resources that you use and there are no up-front fees or termination charges.
AWS provides a fifteen-day free trial allowing you to evaluate the service and generate an accurate cost analysis, before determining if the service meets your requirements.
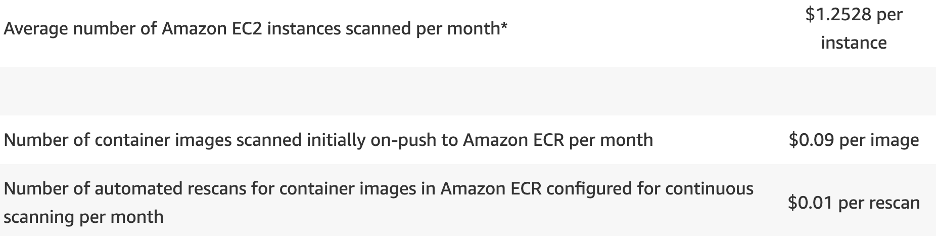
Monthly costs are determined by a combination of two factors: The number of EC2 instances scanned, and the total number of container images initially scanned when pushed into ECR and rescanned over a month.
Image shows Amazon Inspector Pricing
The average number of EC2 instances scanned per month is: the total hours of active, supported instances scanned, divided by the number of hours per month (720 hours on average). For example, if 5 EC2 instances were scanned for 30 days, this would equal $6.25 (5 instances * $1.25 per instance).
For ECR Images, the cost would depend on your image strategy and the frequency that images are built and pushed to ECR. Each scanned image will incur a cost of $0.09. For example: an environment with 10 new container images (10 * $0.09 = $0.90). Assuming that these images are rescanned 10 times per month (100 * $0.09 = $9.00), the total cost would be $9.90.
Integration with AWS Services
AWS Inspector can integrate with other AWS services including AWS Organizations, AWS Systems Manager, AWS Security Hub, and AWS EventBridge. This provides a competitive advantage over many third-party tools that typically lack this integration. We will now discuss each of these in turn.
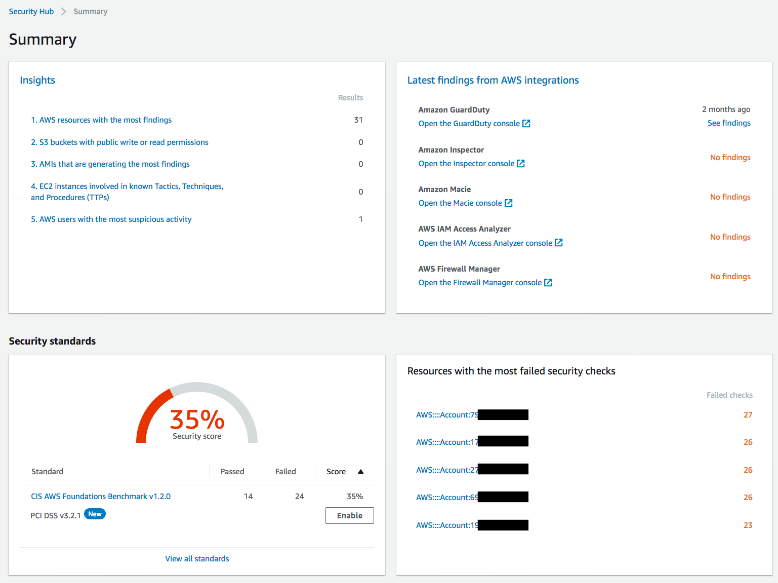
AWS Security Hub
AWS Security Hub provides a comprehensive view of your AWS security posture in comparison to industry best practices. AWS Security Hub can display vulnerability and results analysis obtained from Amazon Inspector, to create a single high-level security dashboard.
Image shows AWS Security Hub Dashboard
Amazon EventBridge
Amazon EventBridge is a serverless event bus that enables event-driven architecture at scale. EventBridge events are created by AWS Services and applications running in AWS. These events can be used to automate workflows and trigger actions such as notifications. Inspector creates events in EventBridge for several cases, including when new findings are discovered, when new findings are aggregated, and when the state of a finding changes. These events can automate the notification and remediation of security issues identified by Amazon Inspector. See here for more information on using Amazon EventBridge.
AWS Systems Manager
AWS Systems Manager Agent (SSM Agent) is a remote management tool that runs on AWS EC2 Instances. One of the tasks that SSM Agent can perform is running security assessments on behalf of Amazon Inspector. This assessment data is later transmitted to Inspector for analysis and Risk Score calculation.
The SSM Agent is preinstalled on many Amazon Machine Images (AMIs) including:
- Amazon Linux Base AMIs dated 2017.09 and later
- Amazon Linux 2
- Amazon Linux 2 ECS-Optimized Base AMIs
- macOS 10.14.x (Mojave), 10.15.x (Catalina), and 11. x (Big Sur)
- SUSE Linux Enterprise Server (SLES) 12 and 15
- Ubuntu Server 16.04, 18.04, and 20.04
- Windows Server 2008-2012 R2 AMIs published in November 2016 or later
- Windows Server 2016, 2019, and 2022
For instances that do not come with the SSM Agent preinstalled, it can be installed as either an OS package (dpkg, apt, dnf, yum, etc.) or downloaded from AWS and installed via script.
Amazon Inspector tutorial
The following section will provide an introduction to Amazon Inspector via a practical demonstration and will include examples of common use cases.
In the AWS Console, enabling Inspector is as easy as a button click:
AWS Console: Enable Amazon Inspector
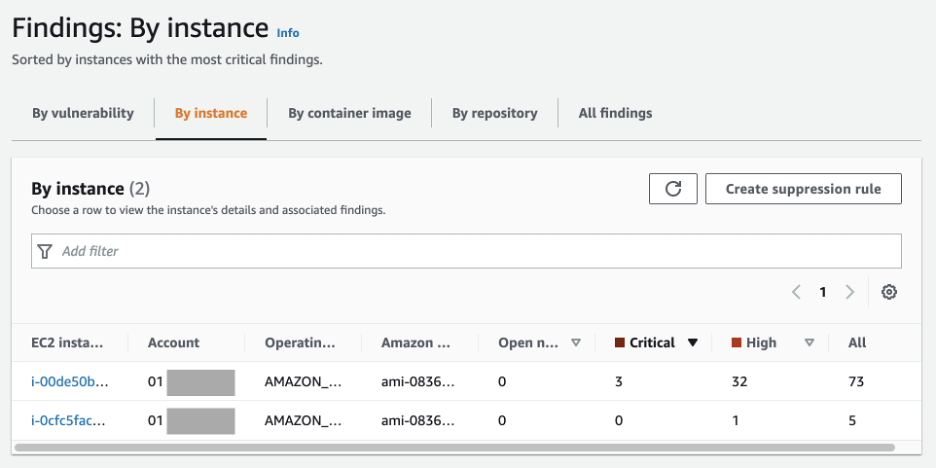
Once Amazon Inspector has performed its initial scan you can view the findings in the console. Findings can be aggregated and viewed by vulnerability, instance, container image or container image repository.
Amazon Inspector Findings: Findings By EC2 Instance
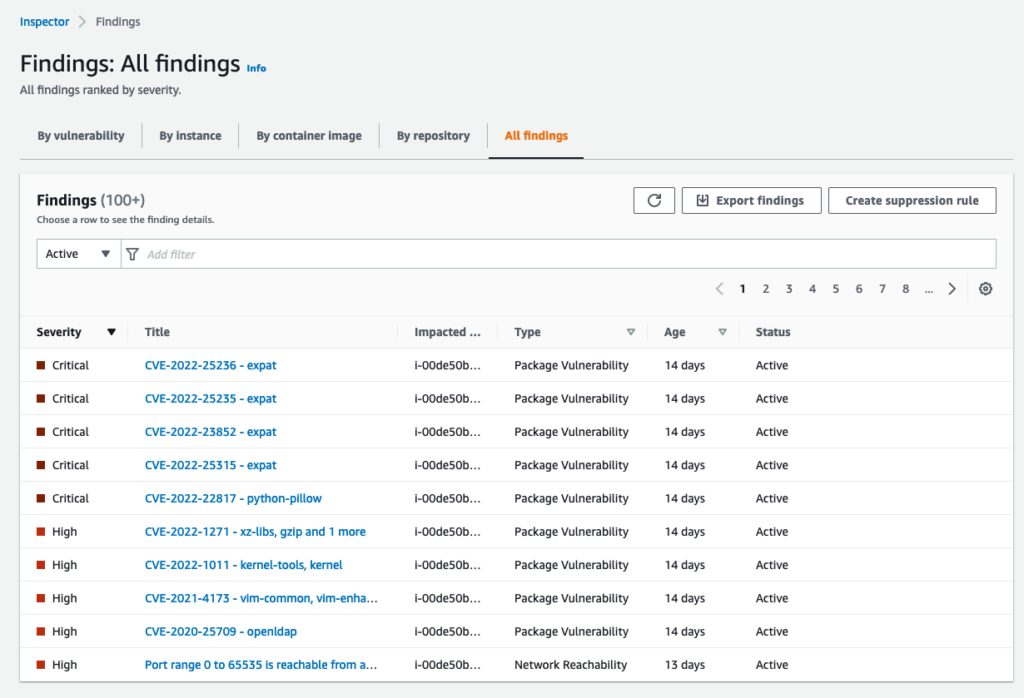
To drill into the details of a finding, just click on the finding name in the column Title.
Amazon Inspector Findings: All Findings
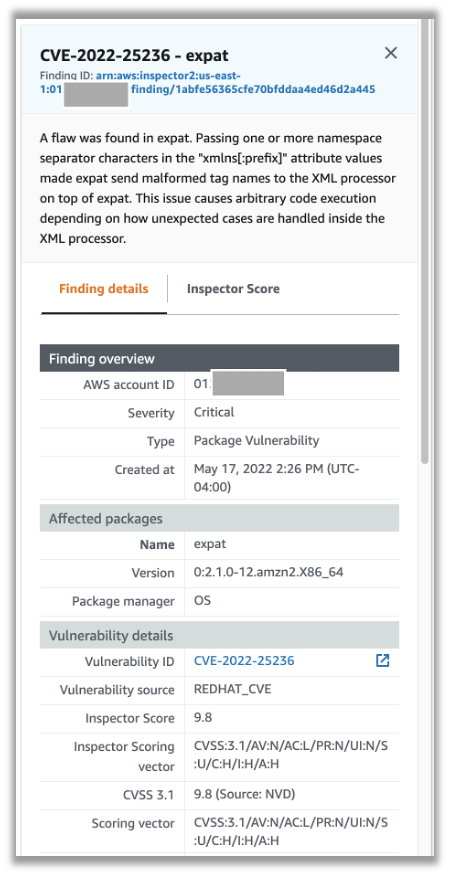
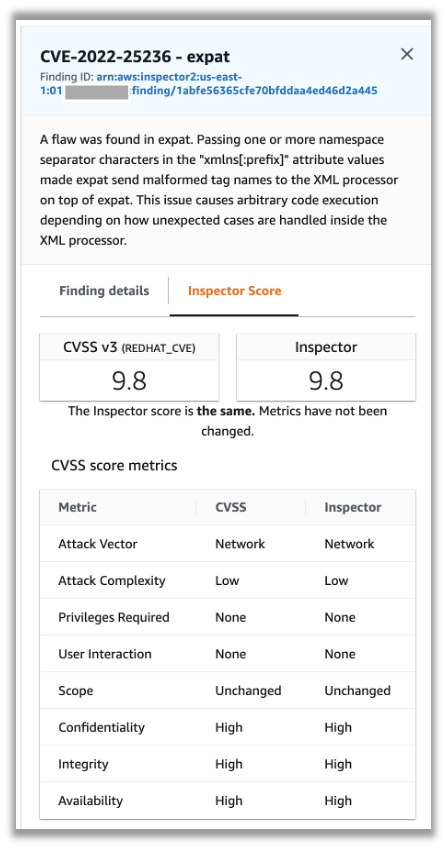
The finding details panel will display the CVE details, affected resources, and the metrics used to calculate the Inspector Risk Score:
Amazon Inspector: Finding Details Panel
Amazon Inspector: Finding Inspector Score
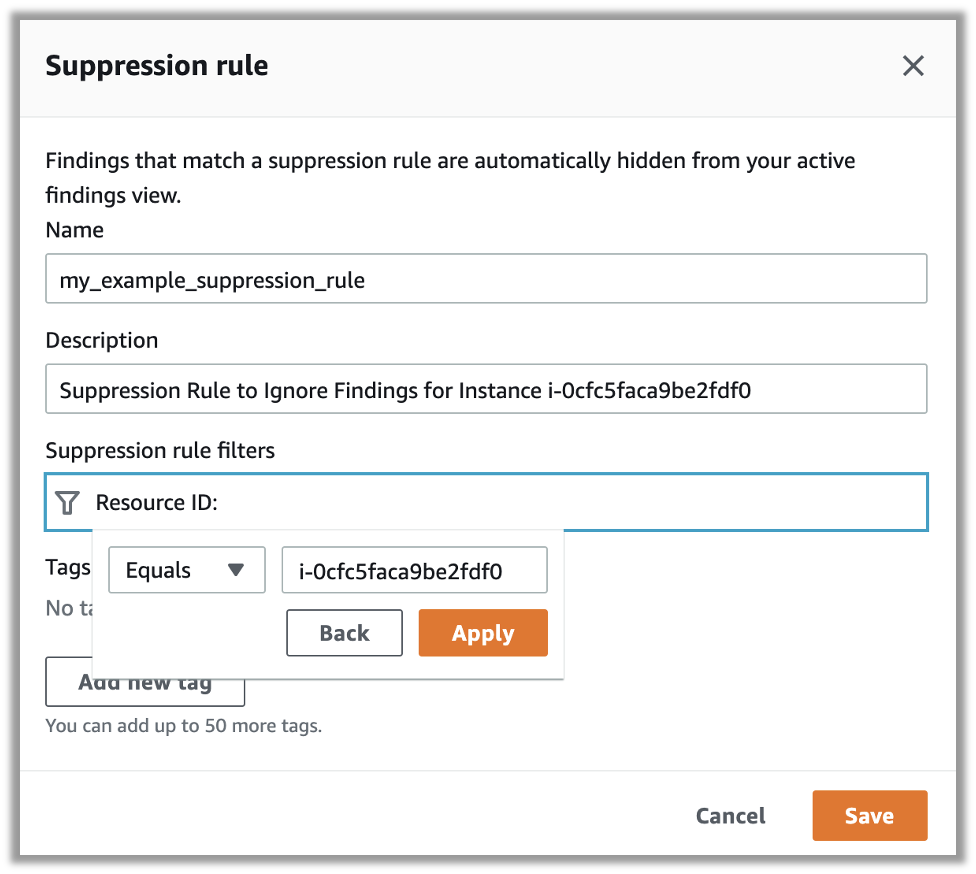
Suppression rules can be created to mute findings that should be ignored. To create a new suppression rule, simply select the Create Suppression Rule button from the console and define a filter to identify the instances or vulnerabilities that you wish to suppress:
Amazon Inspector: Create Suppression Rule
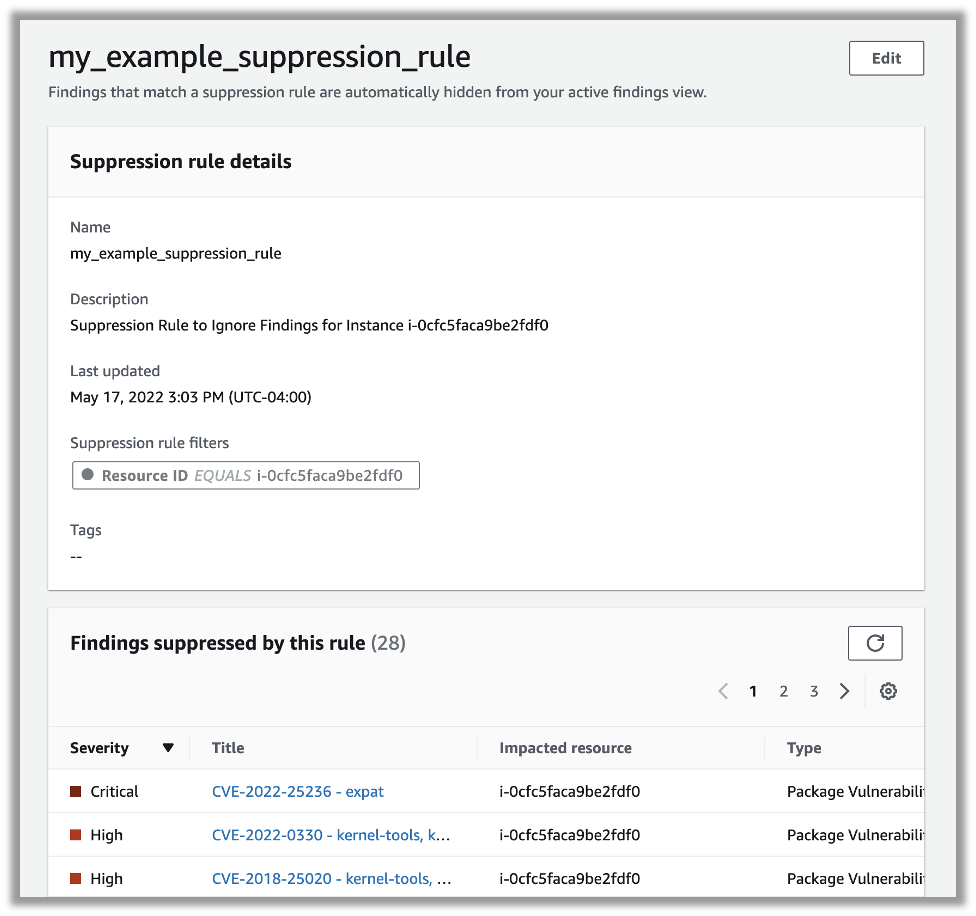
Once created, you can view the details of the suppression rule – including a list of any findings that are to be suppressed:
Amazon Inspector: Suppression Rule Details
Limitations
Information Technology security is a complex and multifaceted discipline that requires a multilevel approach. While Amazon Inspector can help your Information Security strategy, it is not a fully comprehensive or all-in-one solution. You will need additional security tools that can provide:
- penetration testing
- security audits
- secure configuration
- network firewalls
- authentication
- information security
- data encryption
- any other Information Security best practices
Amazon Inspector is limited to the inspection of EC2 instances and ECR images. It does not inspect other services for vulnerabilities, including AWS Lambda, AWS RDS, DynamoDB or S3, and so on.
Furthermore, AWS does not guarantee that Amazon Inspector will identify every possible security issue. The findings generated by Inspector depend on your configuration, assessment template rules packages, the presence of any non-AWS components, and other factors.
It’s also important to remember that AWS operates under a Shared Responsibility Model, where you are responsible for the security of your systems, applications, data, and processes.
Summary
- Amazon Inspector solves several complex technical needs and can help with a comprehensive Information Security strategy when best practices are followed
- Amazon Inspector is a newly re-architected version of Amazon Inspector Classic. The new version of Amazon Inspector expands upon the functionality of the previous classic service, adding support for ECR images, multi-account support via AWS Organizations, and provides continual vulnerability scanning
- do not use an account administrator to manage individual services (such as Inspector) and always follow the principle of least privilege
- Amazon Inspector creates Amazon EventBridge events for new findings, newly aggregated findings, and state changes of existing findings
- with EventBridge events, you can automate notification or remediation tasks to help further reduce your MTTR
- Inspector suppression rules can be used to reduce your signal-to-noise ratio and focus on more critical findings

|
Platform
|
Provisioning Automation |
Security Management |
Cost Management |
Regulatory Compliance |
Powered by Artificial Intelligence |
Native Hybrid Cloud Support
|
|---|---|---|---|---|---|---|
|
AWS Native Tools |
✔
|
✔
|
✔
|
|||
|
CoreStack
|
✔
|
✔
|
✔
|
✔
|
✔
|
✔
|
Conclusion
Amazon Inspector automates vulnerability scanning across several AWS workloads, helping to reduce your MTTR. If your organization's IT infrastructure is in the AWS cloud, Amazon Inspector is an effective solution for proactively identifying security risks, improving protection, and reducing MTTR in the event of an exploit.