AWS Tagging: Best Practices
AWS tags are key-value pairs assigned to AWS resources as a form of additional data called metadata. Each tag is a user-defined or AWS-generated key and value assigned as a label against a resource. A tag is often attached to AWS resources to identify, categorize, organize, filter, or manage them. For example, you can use tags to order resources based on purpose, environment type, owner, etc. Each tag has a tag key (e.g., Name, Environment, etc.) and a tag value (e.g., Panda, Production, etc.) These key-value pairs can be assigned to resources for access control, for example, by using tags as condition keys in IAM policies. Tags can also be fundamental to organizing resources within the AWS Console and make searching and filtering your resources easier. You can even use tagging to allocate expenses against the relevant cost centers!
A well-developed tagging strategy can be vital to effective access control, cost allocation, and general resource management. This article, therefore, aims to provide an in-depth guide to resource tagging. We will discuss several use cases, best practices, and strategies to implement effective tagging policies. Below is an executive summary of the key areas covered in the article.
Executive summary
| Best Practice | Description |
|---|---|
| Resource organization based on tagging | Discusses tagging for resource management |
| Tag-based cost allocation | Measuring costs of AWS resources based on the tags associated with them |
| Managing access in AWS using tags | Explain the use of tags with IAM policies as conditions for access control |
| Use of tags in automation | The use of unique tags in automation for grouped activities |
| Security governance of tagging | Monitoring high-risk assets by using the tags assigned to them |
Organizing AWS resources
Tags serve as a means to organize resources within the AWS Console. You can use tags to search and filter resources by key-value pairs and assign them to resources at any stage. You can also create Resource Groups based on tags to view and manage resources in a consolidated fashion. Doing so helps you view different application data through a single pane of glass, including resources from multiple services and regions.
You can also use tags with service consoles to search for and filter resources. For example, on an EC2 console, you can use a team tag to filter instances hosted by a particular team. The most frequently used tags in Amazon’s EC2 service include owner, team, environment, and stack and can be used in cost analysis, development automation, and application scaling.
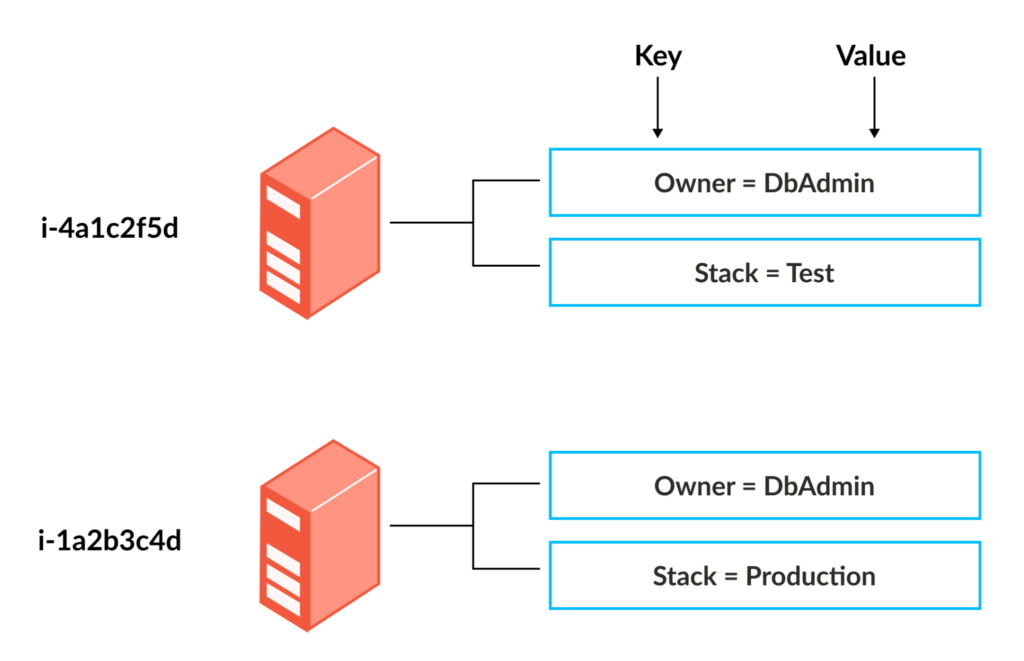
The diagram below shows two tag keys, owner and stack. Each instance has duplicate tag keys but different tag values, which helps organize resources by custom criteria.
Instance tagging (source)
Tagging AWS resources
You can add tags to resources at the point of creation or at a later stage by editing the resource tags directly. Using the resource groups service, you can assign tags to a large group of resources automatically. Tag Editor is a feature that attaches tags to a group of resources at once. Just locate your specific resources and then assign them the desired tags.
It is important to remember that a tag key can have a given value of zero or one, but not multiple values. A good approach is to tag resources automatically by using infrastructure as a code (IaC) or collectively to avoid errors or misconfiguration. We will discuss this practice later in the article.
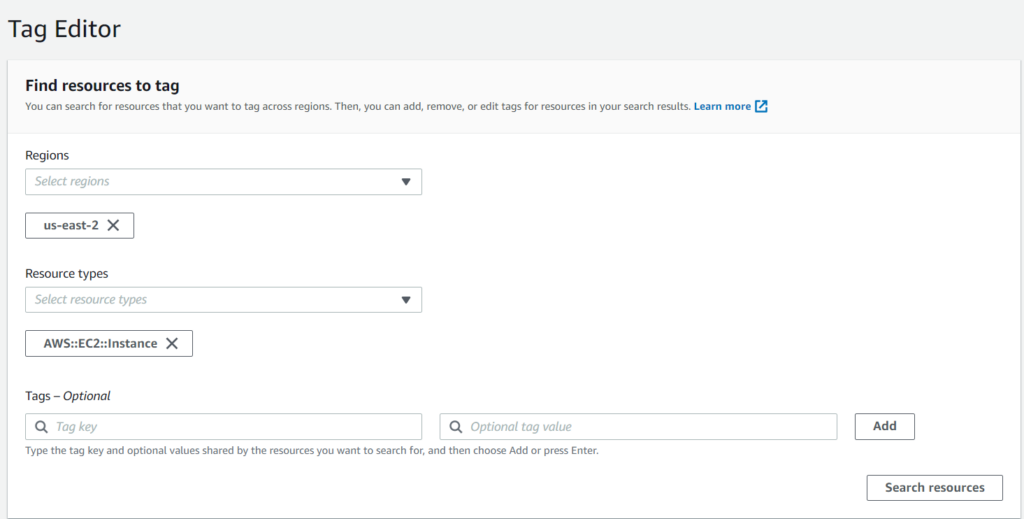
The example below shows how Tag Editor can locate resources by searching for specific criteria, such as “all the EC2 instances in region us-east-2”.
Tag Editor search console
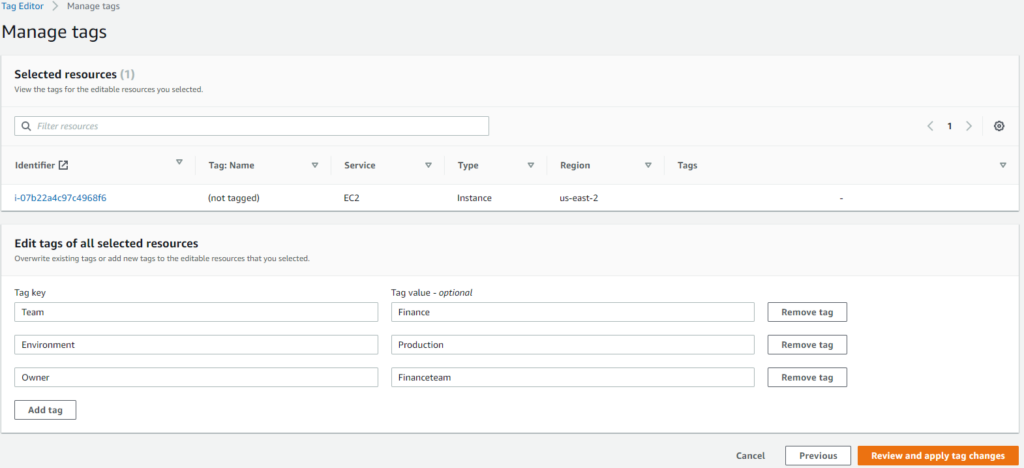
Once you have chosen the right set of resources, you can assign as many as 50 tags to each of them. There are some limitations with tagging though, and we will discuss these later in the article. The figure below shows the Tag Editor UI being used to assign tags to selected resources.
Tag Editor tags management console
You can also assign tags to supported resources by using CloudFormation. The tags can be attached using Tags or the Tagspecfications property of CloudFormation templates.
Tracking costs with tags
Tags are utilized by AWS Cost Explorer and Detailed Billing Reports to categorize costs. In the Cost Allocation Report, you can create Cost Allocation tags to help you organize resource costs. Categorizing costs by tag makes tracking expenditure on your AWS resources easier. Cost reports support two tag types: AWS-generated and user-generated tags.
AWS-generated tags vs. user-generated tags
As the name suggests, AWS-generated tags are created by AWS and are pre-defined. Likewise, user-generated tags are custom-made by the customer based on their needs. You can allow one or both of these tag types to appear in your Cost Explorer and cost allocation reports. AWS-generated tags are denoted by the prefix “aws:” while user-generated tags have the prefix “user:”
When you generate cost reports, the costs of tagged and untagged resources are displayed separately for your analysis. You can use tags to filter your views on the Cost Explorer console. AWS-generated tags include “aws:createdBy” to indicate who created the resource. In contrast, user-defined tags are usually categorized by owners, projects, cost centers, application stack, etc. This categorization allows costs to be broken down and apportioned to various applications and businesses hosted in the same organization or account.
Budgeting alarms based on tags
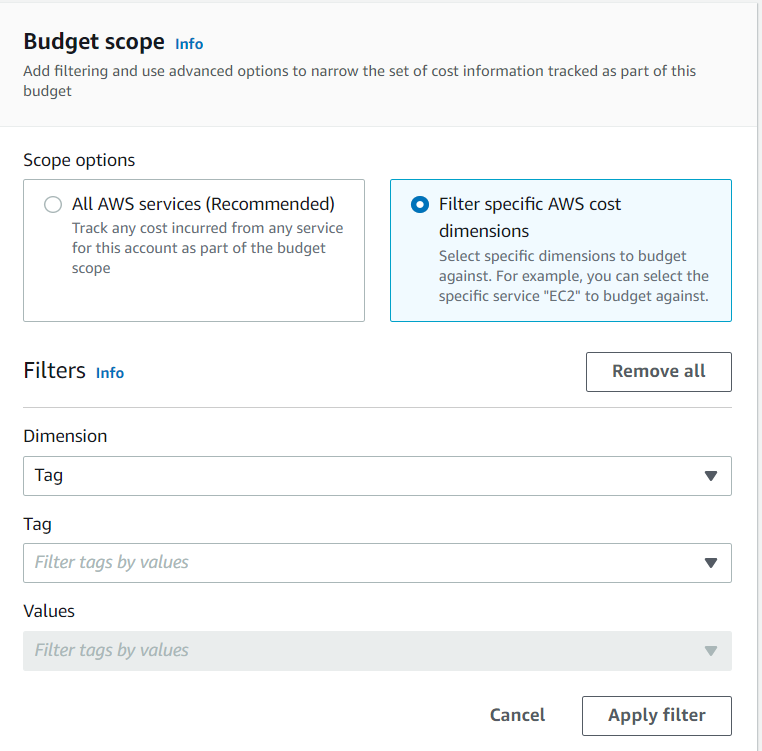
Budgeting alarms are created for cost tracking purposes. You can use tags to filter the costs for a particular environment and configure notifications using SNS channels to notify in case of exceeding costs. With budgeting alarms, you can use any activated tags for filtering. The recommendation is to keep the tagging scheme simple and easy to follow.
Budget scope filters
Using tags in automation
You can use tags to manage resources during automation tasks. Resources can be included or excluded from the automation task based on the assigned tag. For example, you can use Lambda to tag all running instances with an owner tag. You could then run another job that discovers and terminates all instances belonging to that user based on the tag. Automation tasks based on tags can also include
- restricting access to production environments during maintenance
- terminating testing environments after working hours to reduce costs
- identifying resources to be updated or deleted
- automating data backups

|
Platform
|
Provisioning Automation |
Security Management |
Cost Management |
Regulatory Compliance |
Powered by Artificial Intelligence |
Native Hybrid Cloud Support
|
|---|---|---|---|---|---|---|
|
AWS Native Tools |
 |
 |
 |
|||
|
CoreStack
|
 |
 |
 |
 |
 |
 |
Managing access with tags
Tags support attribute-based access control (ABAC). ABAC limits access to resources based on the tags that are passed along with the access requests. Tags are used in IAM policies to define access criteria via condition keys. For example, you can limit access to owners alone by following the IAM policies shared here. See Example 2: Use tags to restrict access to a resource to its “owner”.
Security governance
You can assign security tags to high-risk resources that require additional monitoring. These security tags are then used to allow or restrict access to high-risk resources.
Tagging constraints
For the most part, tags are designed for access control, billing, and administrative purposes. Here are some factors that should be considered when assigning tags.
Basic restrictions
Resources have a maximum limit of fifty tags. Tags are case-sensitive, which should be considered when assigning and filtering resources by tag. A complete list of tag restrictions can be found here.
Sensitive information in tags
Tags should not contain private, personally identifiable information (PII), passwords, secrets, or anything that might be considered sensitive.
Misconfigured tags
Any misconfigured tags (tags with misspelled keys or values, incorrect case, etc.) in your IAM policies may lead to unauthorized access to resources. Automation processes can also break due to misconfigured tags. We recommend that you configure tags using tagging tools to avoid errors.
Privilege escalation using tag-based access control
Tag-based access control can be susceptible to exploitation by insiders with permission to update resource tags. Anyone who can edit the conditions within your IAM policies can also conduct malicious actions. It is therefore recommended to restrict the permissions to your access control tags once they are attached to resources.
Tagging best practices
Develop a consistent tagging strategy
Identify all tag categories required by your business. Often, tags are categorized into:
- technical
- automation
- business
- security
After defining your categories, you should design a simple tagging strategy for all tag types. We recommend using a standardized, case-sensitive format across all resource types. Use proactive governance tools, such as CloudFormation, to assign tags to resources at the point of creation. Also, you can use reactive governance tools, such as Resource Groups and AWS Config, to update any misconfigured tags.
Enforce a consistent tagging policy across all accounts, products, and applications. Using the same tagging methodology for all AWS resources helps organize and manage resources more effectively.
Use tag policies for standardization and enforcement
Tagging policies are created via AWS Organizations to enforce the creation of standardized tags across the business. Enforcing standardization is accomplished by comparing tags against authorized key/values pairs.
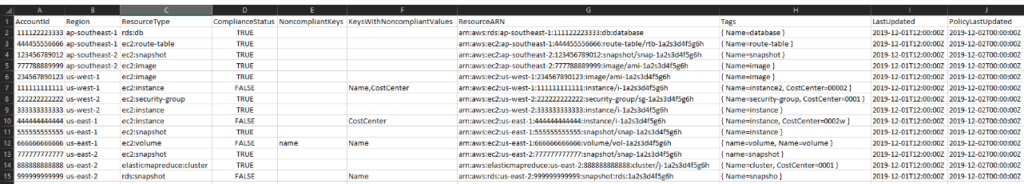
Non-compliant tags are flagged, and reports can be generated that display compliance at the account and organization levels. Once all tags are compliant, tagging policies can be used to enforce this state.
Compliance report (source)
Prevent the creation of tagless resources
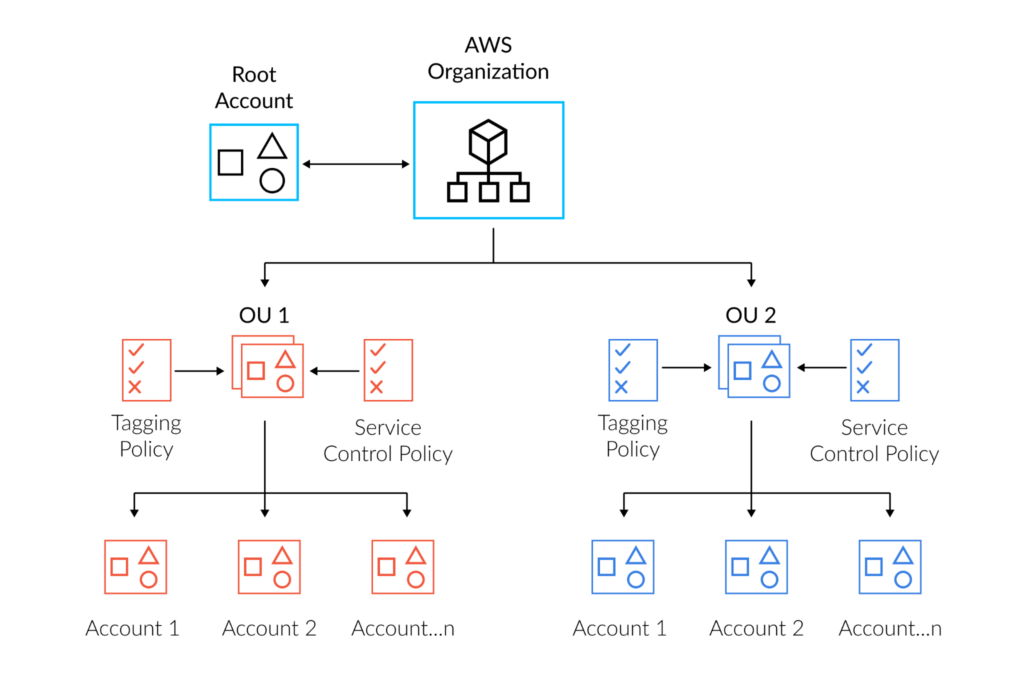
You can use Service Control Policies (SCPs) to prevent the creation of new untagged resources. Using both tagging policies and SCPs together ensures that the correct tags are used and that no resource is left untagged. For guidance, please see here. The diagram below shows an AWS Organization and its accounts, tagging policies, and SCPs applied at the Organizational Units(OUs) level.
SCPs and tagging implementation (source)

|
Platform
|
Provisioning Automation |
Security Management |
Cost Management |
Regulatory Compliance |
Powered by Artificial Intelligence |
Native Hybrid Cloud Support
|
|---|---|---|---|---|---|---|
|
AWS Native Tools |
 |
 |
 |
|||
|
CoreStack
|
 |
 |
 |
 |
 |
 |
Conclusion
A well-developed strategy for tagging and enforcing tagging compliance helps improve:
- management of resources
- effective cost analysis
- access control
- security governance
Conversely, misconfigured tags can result in automation breakage, privilege escalation attacks, and poor budgeting. Therefore, a strategy is needed to prevent the creation of untagged resources and to enforce consistent tagging. To this end, tagging policies and SCPs can be very effective. However, nothing remains static, and your tagging strategy should be periodically reviewed and compared against evolving requirements. If in doubt, the best practice from AWS states:
“Use too many tags rather than too few….”
Using tags is essential to good infrastructure management, and combining practice, planning, and preparation will ultimately lead you to discover what approaches work best for your organization.