Azure Security Tools: A Comprehensive Overview
Azure is an enterprise cloud platform that hosts customers’ identity, application, compute, storage, and networking solutions. In addition, it provides native security tools and capabilities to enable customers to protect their workloads and respond to cybersecurity threats, which are a top priority for organizations of all sizes, industries, and locations.
Azure also integrates with third-party solutions to augment overall organizational security postures. Companies can leverage Azure native solutions, purchase third-party solutions, or use both. They should consider various factors to select the right solution, including workload type and size, business requirements, pricing, and support.
This article lists and explains key Azure security tools and management solutions across several areas. It also explores 15 native Azure solutions.
Executive summary
The table below outlines the key concepts this article covers to help readers understand.
| Concept | Description |
|---|---|
| Azure Bastion | A platform as a service (PaaS) tool that enables secure RDP/SSH connectivity to Azure virtual machines directly from the Azure portal over TLS. |
| Azure Firewall | A managed firewall service that filters and analyzes traffic at Layers 3, 4, and 7 of the OSI model. Azure Firewall can provide alerts and deny traffic from/to known malicious IP addresses and domains in real time. |
| Conditional Access (CA) | Azure AD Conditional Access enables organizations to control access to business applications based on sign-in signals, which include user, device, location, and real-time risk information. Safe sign-ins are allowed access, while unsafe sign-ins are denied. |
| Microsoft Defender for Cloud | A Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP) platform for cloud and on-premises workloads. |
| Microsoft Sentinel | A cloud-native platform for security information and event management (SIEM) and security orchestration, automation, and response (SOAR). |
| Network Security Group (NSG) | A basic firewall service that filters inbound and outbound traffic to and from Azure resources based on a 5-tuple hash. NSGs work on Layers 3 and 4 of the OSI model. |
| Private Link | A private endpoint in a VNet to enable access to Azure PaaS services securely and privately, eliminating the need for public internet exposure to get to the services. |
| Privileged Identity Management (PIM) | PIM provides a time-based and approval-based Azure AD role activation service to manage, control, and monitor access to critical resources in the tenant. |
| Role-Based Access Control (RBAC) | RBAC is an authorization system built on Azure Resource Manager to grant users fine-grained access to Azure resources. |
| Secure Access Signature (SAS) | A signed URI that provides secure delegated access to resources in Azure storage accounts. |
| Web Application Firewall (WAF) | WAF provides centralized protection of web applications from common threats such as cross-site scripting attacks, session hijacking, SQL injection, and malicious bots. |
Identity and Access Management (IAM)
User and device identity are considered the modern security perimeter of the cloud. Azure Active Directory (AD) is the Microsoft cloud-based directory service that manages authentication and authorization for Microsoft cloud services such as Office 365, Intune, and Dynamics 365. In addition, Azure AD provides several security and compliance tools for customers to secure identities and manage access.
Azure AD Conditional Access
Conditional Access enables customers to grant or deny access to business applications and admin portals based on defined security criteria such as user sign-in location, device compliance, and calculated risks. Conditional Access brings together signals to make decisions and enforce required security policies. Unsafe sign-ins are blocked, while safe sign-ins are granted access. However, unsafe sign-ins can be given access based on completing additional security requirements such as the following:
- Multi-factor authentication (MFA): The user must provide a second factor to complete the sign-in process.
- Intune Compliance: The device must be Intune-compliant as per Intune compliance policies.
- Hybrid Azure AD Joined Device: The device must be joined to Azure AD.
- Approved Client App: The tenant must authorize the app for sign-ins. For example, tenant admins can allow IOS and Android devices to sign in but reject macOS devices.
Azure AD Conditional Access signals and policies (Source)
Azure AD Identity Protection
Identity Protection detects numerous sign-in risks, including:
- Anonymous IP address use
- Atypical travel
- Malware-linked IP addresses
- Unfamiliar sign-in properties
- Leaked credentials
- Password spraying
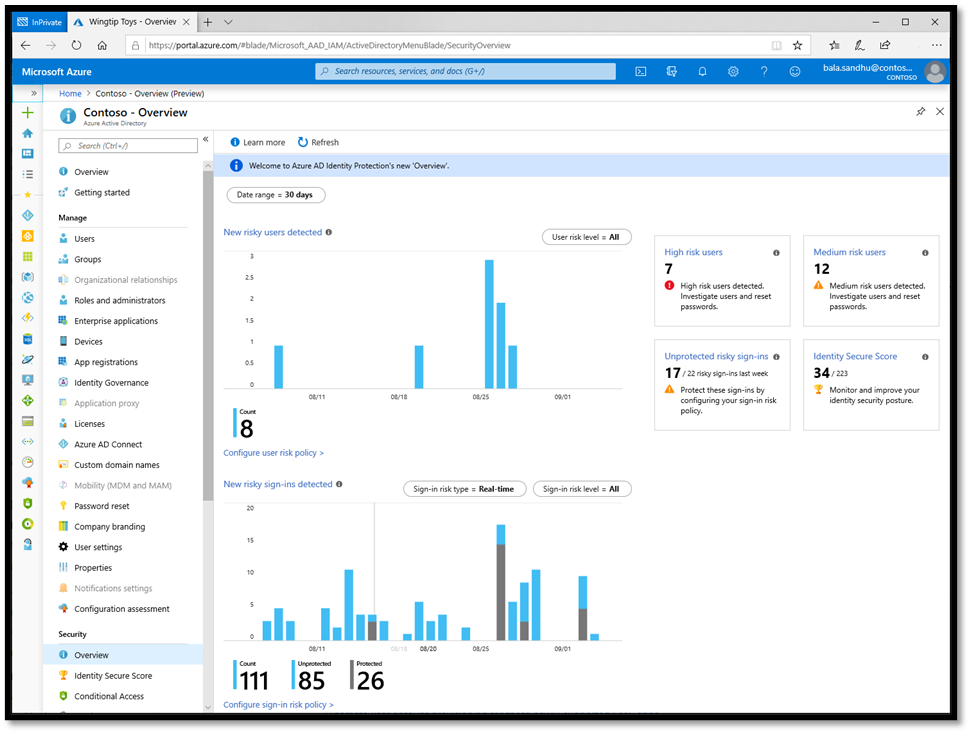
Identity Protection is an integral part of Azure AD Conditional Access. The risk signals can trigger remediation efforts — such as requiring users to perform MFA or reset their passwords — or deny access. Microsoft provides organizations with three reports to investigate security risks in their environments: risky users, risky sign-ins, and risk detections. Organizations need to explore the events in the reports to better understand and identify weak points in their security strategies.
Azure AD Identity Protection reporting (Source)
Azure AD Privileged Identity Management
Privileged Identity Management (PIM) helps organizations manage, control, and monitor access to resources and admin roles in Azure, Azure AD, Office 365, and Intune. PIM provides just-in-time and approval-based access to mitigate the risks of excessive or unnecessary access permissions, thus providing identity governance.
Assigning roles in PIM (Source)
Azure Role-Based Access Control
Azure Role-Based Access Control (RBAC) helps organizations manage access to Azure resources. Built upon Azure Resource Manager, RBAC is an authorization system providing granular access management to Azure resources. For example, admins can assign Azure roles for users to manage all virtual networks in a subscription, all resources in a resource group, or login rights to a virtual machine. Admins can also assign Azure roles for applications to access specific resources in a resource group.
In RBAC, a security principal (user, group, service principal, or managed identity) is assigned a role (collection of permissions) to a scope (set of resources to which the access applies). Azure AD supports built-in and custom roles. Built-in roles include owner, contributor, reader, backup operator, security reader, virtual machine user login, and storage blob contributor. In addition, Azure admins can assign Azure roles to a management group, subscription, resource group, or resource.
Identity and access management solutions in Azure have license implications. The diagram below shows the different capabilities, corresponding security tools, and minimum license requirements.
Identity and access management capabilities, tools, and license requirements
Azure Attribute-Based Access Control
Azure Attribute-Based Access Control (ABAC) builds on RBAC to provide more fine-grained access control to Azure resources. ABAC helps reduce the number of role assignments and secures access rights to meaningful business needs.
Azure storage admins can add ABAC conditions on built-in or custom role assignments with blob storage or queue storage data actions. Admins can use attributes like account name, blob index tags, blob path, container name, current version, snapshot, and version ID.
For example, ABAC enables Azure storage admins to restrict read access to Azure blobs that are tagged with “project name = sales” or limit write access to blobs in a container named “marketing container” with a path “uploads/corp.”
ABAC role assignment conditions
Identity Access
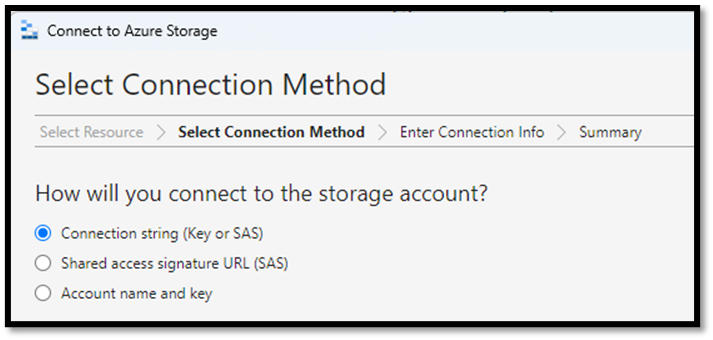
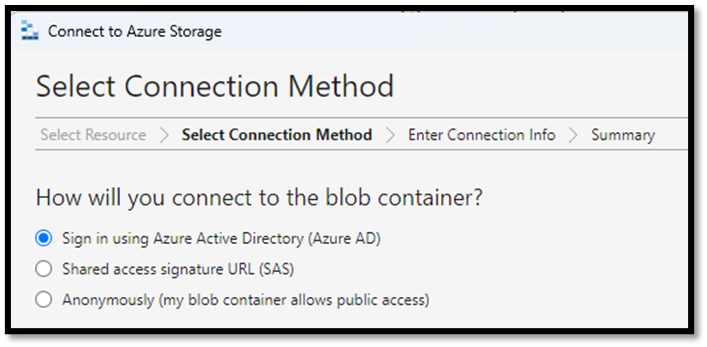
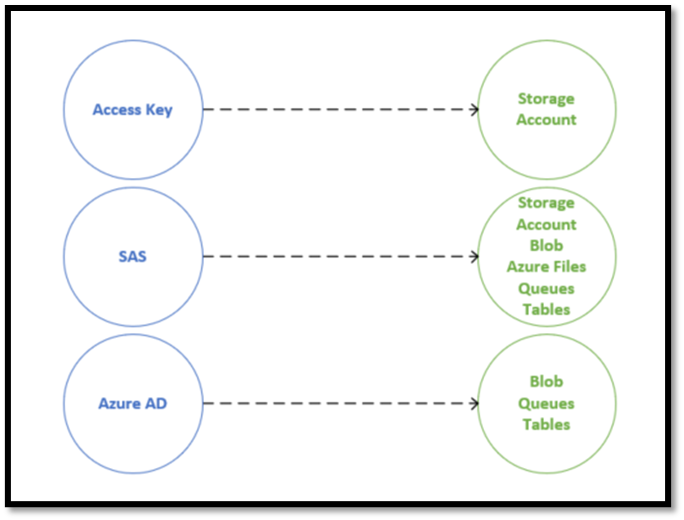
Azure provides organizations with secure connectivity methods to securely access their storage accounts. For example, storage accounts support account keys, shared access signature (SAS), and connection string methods. In addition, blob storage supports Azure AD and SAS for secure access and anonymous connections for public access.
Azure storage account and blob connectivity methods
Storage Access Keys
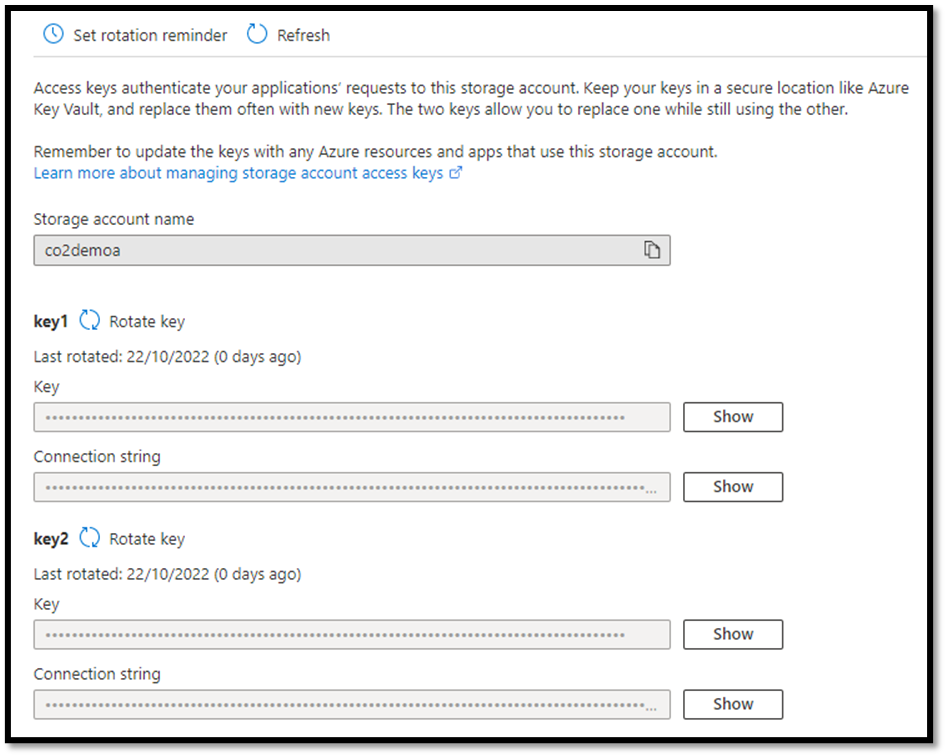
Azure generates two 512-bit access keys for storage accounts that admins can use to authorize access to data in the storage account. However, these keys must be kept safe and rotated regularly. Azure Key Vault is a safe place for storage account key management and rotation. In addition, admins can use the “set rotation reminder” option in Azure storage keys to get notified when the keys need to be rotated.
Azure storage account keys
Setting a reminder for storage account keys rotation
Shared access signatures
A shared access signature (SAS) is a signed URI that grants restricted access rights to Azure storage resources, such as read access to blob storage and list access to Azure files. In addition, SAS includes service access start and end dates and times, protocols, and network restriction options.
Azure Storage supports user delegation SAS, service SAS, and account SAS. A user delegation SAS is secured by Azure AD and is only supported on blob storage. A service SAS is signed with the storage account key and supports all storage types, blob, files, tables, and queues. Like a service SAS, account SAS is secured with the storage account key. Account SAS grants access to resources in various storage services.
SAS generation settings
Azure AD
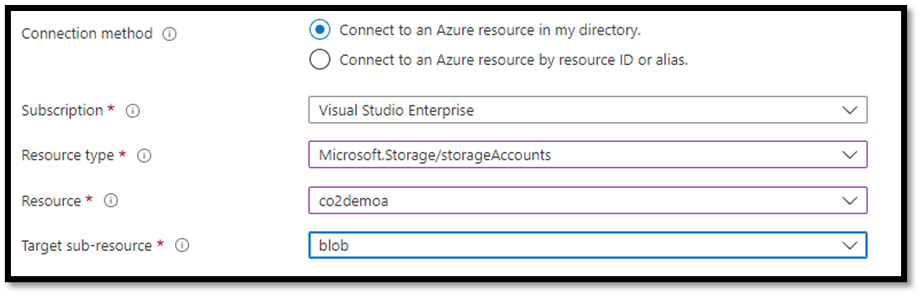
Microsoft recommends using identity-based authorization based on Azure AD to access Azure storage account services. For example, storage admins can use RBAC to grant users, groups, or applications access rights to blob, queue, and table services. Moreover, the access rights can be scoped to the levels of an individual container, queue, or table.
Azure AD integration is an easy-to-use access method and provides greater security than SAS and Access Keys. Azure AD issues the security principal with an OAuth 2.0 token, which the storage service accepts. This authorization technique removes the need for access and SAS keys.
Azure AD RBAC built-in storage roles
Using an authenticated Azure AD user account to upload files to blob storage
Azure storage access supports access keys, SAS, and Azure AD methods. The diagram below shows the storage access methods and supported services.
Storage access methods and supported services
Network access
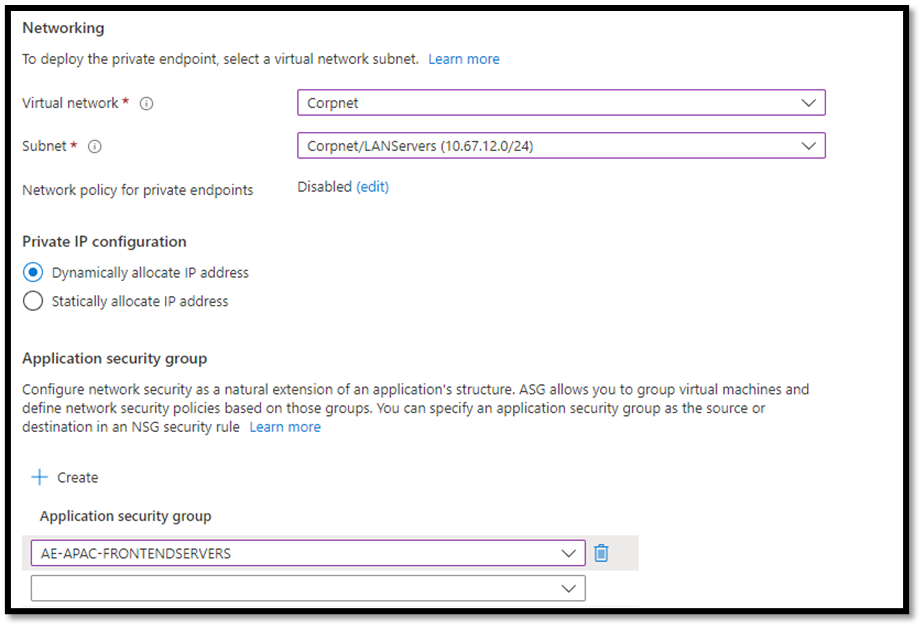
Storage admins can create a private endpoint to secure all traffic between Azure Virtual Network (VNet) and the storage account. A private endpoint assigns a private IP address from the VNet to an Azure storage account. Only applications requesting data over the private endpoint can access the data in a storage account.
Additionally, admins can restrict access to Azure storage accounts to specific IP addresses, IP ranges, subnets, or resource instances of some Azure services.
Restricting network access to Azure VNets and IP addresses
Configuring a storage service endpoint on a subnet in a VNet
Encryption
Azure Storage data is encrypted in transit and at rest. The data transmitted from client applications to Azure storage is encrypted using Transport Layer Security (TLS). Azure Storage uses TLS 1.2 on public HTTPS endpoints.
Azure Storage uses service-side encryption (SSE) to encrypt the data hosted in the cloud. The information is encrypted and decrypted transparently using 256-bit AES encryption, using Microsoft-managed keys by default.
SSE encryption settings on Azure storage account
For flexibility and added security, Azure storage supports:
- SSE customer-managed keys
- Infrastructure-level encryption
- Client-side encryption for blobs
- Azure disk encryption for Windows and Linux VMs
- SMB 3.0 encryption
Azure Compute
Azure Compute provides an on-demand infrastructure to build Windows and Linux virtual machines (VMs) to run business applications and services. Securing access to Azure VMs is paramount, as are ensuring confidentiality and applying real-time malware protection to the infrastructure.
Azure Bastion
Azure Bastion is a platform as a service (PaaS) offering providing secure RDP/SSH connectivity to Azure VMs. Azure Bastion is provisioned inside a VNet and delivers TLS connectivity to all VMs in the VNet.
Users connect to the Azure portal using any HTML5 browser to remotely access Azure VMs. No special Network Security Group (NSG) configuration is required on the Azure Bastion subnet, and no public IP is needed on the VMs.
Azure Confidential Computing
Azure confidential computing offers confidential VMs based on AMD processors with SEV-SNP technology. These VMs provide robust hardware isolation among virtual machines, hypervisors, and host management code. They also support confidential OS disk encryption, dedicated virtual Trusted Platform Module (TPM) instances, and secure boot capability similar to trusted launch for Azure VMs.
Tenants with high security and confidentiality requirements can use confidential VMs, which support Ubuntu 20.04 LTS, Windows Server 2019, and Windows Server 2022. They are limited to DCasv5-series, DCadsv5-seriesECasv5-series, and ECadsv5-series VMs.
Microsoft Antimalware
Microsoft Antimalware for Azure is a real-time protection solution that helps identify and remove spyware, viruses, and other malicious software from Azure VMs. It provides active protection, scheduled scanning, malware remediation, signature updates, and reporting. By default, the Microsoft Antimalware client and service are installed in a disabled state in all supported Azure guest operating systems. Microsoft Antimalware is not installed by default in Azure VMs and is available as a security extension install feature in the Azure Portal.
Networking
Network security and traffic flow control in and out of Azure are imperative for cloud security architecture. Azure Firewall and Network Security Groups (NSGs) are the Microsoft solutions for Azure network security. In addition, private links secure traffic flow from VNet to Azure PaaS services.
Azure Firewall
Azure Firewall is a scalable, intelligent firewall service in Azure that provides inbound and outbound traffic inspection, filtering, and monitoring. It supports destination network address translation (DNAT), application, and network rules as well as TLS inspection, IDPS, URL filtering, and web categories.
Network Security Groups
An NSG is a group of security rules that filter inbound and outbound traffic to and from Azure resources based on a 5-tuple hash. Allow or deny decisions are processed in priority order based on these fields: Source, Source Port, Destination, Destination Port, and Protocol. These decisions apply to the traffic flow in and out of VNet subnets and network interface cards (NICs). Delve deeper into NSGs in our detailed article.
Private Link
Azure Private Link enables organizations to access Azure PaaS services and hosted customer and partner services over a private endpoint. The private endpoint is a network interface that utilizes a private IP address from your VNet. In essence, Azure private link brings the service, such as Azure Storage, into your VNet, providing secure and private connectivity.
Network traffic from the VNet to Azure PaaS services traverses the Microsoft Azure backbone network, eliminating the need for public internet connectivity.
Azure Private Link provisioning and Azure storage endpoint configuration
Web Application Firewall
Azure secures access to business applications as they store business value on the cloud platform. Apps security in Azure entails securing web applications via isolated networks to identify and block unsolicited traffic.
The Web Application Firewall (WAF) provides centralized protection of web applications from common threats such as cross-site scripting attacks, session hijacking, SQL injection, and malicious bots. As the first line of defense, WAF resolves known threats faster centrally than doing so for each application. There are customized features for WAF depending on which service it is deployed: Azure Application Gateway, Azure Front Door, and Azure Content Delivery Network (CDN).
Operations
Security operations help customers see their environments’ overall security postures.
Microsoft Defender for Cloud
Microsoft Defender for Cloud is a Cloud Security Posture Management (CSPM) and Cloud Workload Protection Platform (CWPP) solution for Azure, on-premises, and multi-cloud resources.
Defender for Cloud’s continuous assessment of the environment’s security posture helps identify, track, and report vulnerabilities. In addition, the platform recommends guided actions to remediate and protect workloads based on industry and vendor security best practices. Finally, Defender for Cloud detects and resolves threats to resources and services to stop security events from developing.
Microsoft Defender for Cloud dashboard
To help improve the security posture of the environment, Defender for Cloud continuously assesses the environment and generates a secure score based on the number of vulnerabilities and risks it finds. The secure score is a percentage, with a high score indicating a lower identified risk level.
Defender for Cloud includes workload-specific advanced and intelligent protections. These Defender plans help alert security admins about suspicious activities related to each specific workload. Below are a few examples of Microsoft Defender plans:
- Defender for Servers
- Defender for Storage
- Defender for SQL
- Defender for App Service
Microsoft Defender for Cloud security score, attack path, and active recommendations
Microsoft Sentinel
Microsoft Sentinel is a hybrid solution encompassing concepts of both security information and event management (SIEM) and security orchestration, automation, and response (SOAR). It delivers intelligent security analytics and threat intelligence across the enterprise. In addition, Microsoft Sentinel provides attack detection, threat visibility, proactive hunting, and threat response solutions.
Microsoft Sentinel collects data from users, devices, and applications, detects and investigates threats using analytics and threat intelligence, hunts for suspicious activities, and responds to incidents rapidly via built-in orchestration and automation.
Using AI and more than 100 connectors to help security teams prioritize the most critical incidents, Microsoft Sentinel incorporates user and entity behavior analytics (UEBA) and rich SOAR capabilities.
To help reduce noise, Microsoft Sentinel uses analytics to correlate alerts to real threat incidents. In addition, Microsoft Sentinel includes correlation and machine learning rules and templates to assist security teams in connecting the dots and working on potential high-impact security incidents.
Microsoft Sentinel incident dashboard
Azure Advisor
Azure Advisor offers personalized, actionable recommendations that optimize cost, security, reliability, operational excellence, and performance. In addition, Azure Advisor helps organizations optimize their deployments based on Microsoft best practices. It collects resource configuration analysis and usage telemetry data from your Azure tenant and recommends solutions based on Microsoft best practices.
To help implement the recommended solutions, Azure Advisor links the recommendations with remediation steps. Security admins, for example, can follow the provided step-by-step guidance to implement the suggested solutions. Remediations can also be postponed or removed if they are not applicable to their environment.
Azure Advisor dashboard
Azure Advisor security impacts and recommendations
Third-Party Tools
Azure built-in security tools are powerful and cover a massive spectrum of cloud and on-premises protection needs. However, they may fall short of some requirements, such as provisioning automation, regulatory compliance, and AI integration.
Azure integrates with enterprise third-party tools to complement its offering and strengthen customers’ security posture in the cloud. CoreStack NextGen Cloud Governance is one example of Azure Marketplace solutions.
Azure Marketplace: CoreStack NextGen Cloud Governance
|
Platform
|
Provisioning Automation |
Security Management |
Cost Management |
Regulatory Compliance |
Powered by Artificial Intelligence |
Native Hybrid Cloud Support
|
|---|---|---|---|---|---|---|
|
Azure Native Tools |
✔
|
✔
|
✔
|
|||
|
CoreStack
|
✔
|
✔
|
✔
|
✔
|
✔
|
✔
|
Learn more about Azure security tools
Azure provides powerful and effective security tools to help customers protect their cloud-hosted identity, application, compute, storage, and networking solutions while integrating with third-party solutions.
Gain deeper insight into Azure security tools through the chapters below.
Chapter 1: Azure Shared Responsibility Model
Understand the shared responsibility model, examples of how customers should leverage the model to secure their data in Azure and Office 365, and deployment best practices.
Chapter 2: Azure Firewall vs. NSG
Azure Firewall and NSG provide superior “defense in depth” network security. Azure Firewall provides threat protection for running workloads, while Network Security Groups (NSGs) filter network traffic among Azure resources.
Chapter 3: Azure NSG
Network security groups (NSGs) are one of the simplest resources to deploy within the Azure ecosystem. Learn how to correctly configure them and seven recommendations to follow when securing the resources that host your applications and data.