Cloud Security Governance Key Concepts
Ensuring the security of digital assets and data has become increasingly important for organizations today. Identity and access management (IAM), data encryption, network security, monitoring, and compliance are the security pillars that protect against cyber threats and data breaches. It is crucial to understand the importance of the various security elements and how they contribute to a comprehensive cybersecurity strategy.
This article explores five key pillars of effective cloud security governance, along with practical examples and implementation ideas for each pillar.
Summary of key cloud security governance concepts
| Security Pillar | Benefits |
|---|---|
| Identity and access management (IAM) | Manage user identities, authentication, authorization, and access to cloud resources and prevent unauthorized access. |
| Data encryption | Protect sensitive data in cloud environments by encrypting all sensitive information at rest and in transit. |
| Network security | Mitigate threats like malware, phishing, and DDoS attacks and secure cloud networks by implementing network security protocols. |
| Monitoring and audit | Track user activity, system logs, and network traffic to identify anomalies or suspicious behavior and minimize the impact of a security breach. |
| Security compliance | Avoid legal and financial penalties by ensuring cloud security policies and practices are consistent with regulations like HIPAA and GDPR. |
Identity and access management
Defining robust policies to prevent unauthorized access to sensitive data and cloud resources is a critical step in securing a cloud environment. Your cloud security governance policies should clearly define access controls, including who has access to what data and under what conditions access is granted. Here are some guidelines you can follow:
- Use a service account to own or control public cloud accounts and provide better security and management.
- Administer subscriptions/accounts/projects through groups rather than individual users.
- Limit the owner role/root user to admin groups only
- Give root access to individual users on a case-by-case basis.
- Use service principal name (SPN) to restrict access to applications and cloud resources.
- Assign the Secret rotation for one year where applicable, for added security.
Implementing and using multi-factor authentication (MFA) is another critical security measure for cloud resources. MFA ensures users provide two or more forms of authentication before accessing cloud resources. For example, a password and a code are sent to their mobile device or generated by an authentication app. This ensures an extra layer of security to protect against unauthorized access and potential data breaches.
Data encryption
Encrypting sensitive information in your organization, whether at rest or in transit, is extremely important to secure your resources and prevent unforeseen data breaches.
Encryption can be custom-administered on all major cloud platforms. Considering AWS as one of the most popular hyperscalers, here is an example of configuring encryption through AWS Key Management Service (KMS).
Configuring encryption for AWS Cloud security governance
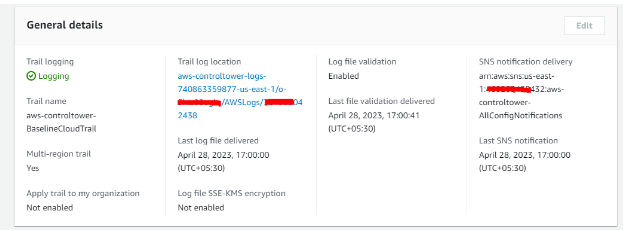
For example, AWS CloudTrail is a service provided by Amazon Web Services that captures the AWS API calls made within an account and grants access to these logs to users and resources per the IAM policies. AWS KMS is another managed solution that aids in generating and managing encryption keys used for securing account data. The service utilizes Hardware Security Modules (HSMs) to ensure that encryption keys remain secure.
You can perform the following to configure CloudTrail to use keys generated by KMS.
- Sign in to the AWS Management Console and open the CloudTrail console at https://console.aws.amazon.com/cloudtrail
- In the left navigation pane, choose `Trails` and click on it.
- Under ‘Log file SSE-KMS encryption’, select ‘Enabled’ under ‘Log file’.
- Save it after selecting an existing CMK and making sure the CMK is located in the same region as the S3 bucket.
Besides following the steps through Management Console, you can configure CloudTrail to use SSE-KMS using the following commands.
aws cloudtrail update-trail --name --kms-id aws kms put-key-policy --key-id --policy
Network security
Network Security protects the network infrastructure and connected devices from attacks, unauthorized access, or disruptions. Here are some essential tips when implementing network security as part of your cloud security governance.
- Monitor cross-region connectivity for securing your cloud workloads.
- Create and use network segmentation policies when the PROD and Non-Prod environments are separated.
- Enable bandwidth throttling in replication tools for improved performance.
- Use private link services to secure the connectivity of your PaaS resources.
Configuring network components for AWS Cloud security governance
Although the fundamental steps of securing components differ for each CSP, in the following example, we apply security policies on an AWS S3 bucket:
You have the option to set permissions at the Amazon S3 bucket level by creating a bucket policy that restricts access to objects only through HTTPS. By default, Amazon S3 permits both HTTP and HTTPS requests. To enforce access to S3 objects solely via HTTPS, you must explicitly deny access to HTTP requests. Follow these steps to configure the above using the AWS console.
- Log in to AWS Management Console and open the Amazon S3 console using https://console.aws.amazon.com/s3/
- Click on the Bucket name.
- Click on ‘Permissions.'
- Under ‘Bucket Policy', Click Edit
- Create a bucket policy that restricts access to objects only through HTTPS by adding the following to the existing policy:
{ "Sid": ", "Effect": "Deny", "Principal": "*", "Action": "s3:GetObject", "Resource": "arn:aws:s3:::/*", "Condition": { "Bool": { "aws:SecureTransport": "false" } } } - Save.
- Repeat for all the buckets in your AWS account that contain sensitive data.
Apart from performing it through the management console, you can also use Policy Generator or AWS CLI.
Ultimately, the choice between using a CLI or a management console comes down to personal preference, as well as the specific needs and goals of the user. For example, some users may prefer the speed and efficiency of a CLI, while others prefer the ease of use and accessibility of a GUI or management console.
Monitoring and audit
Monitoring and auditing in the public cloud is the process of continuously tracking cloud resources and activities to detect security threats, identify potential vulnerabilities, and ensure compliance with regulations and policies. They provide a comprehensive approach to cloud security governance.
Monitoring
Monitoring involves tasks like:
- Continuously observing and analyzing public cloud systems and applications to detect suspicious or anomalous activities.
- Tracking user activities, network traffic, and system logs.
By detecting potential security breaches early, monitoring enables prompt response and mitigation of any security incidents. Additionally, it helps to identify vulnerabilities that hackers or insiders could exploit.
Audit
An audit involves conducting a systematic and independent review of public cloud systems and applications to evaluate their compliance, effectiveness, and efficiency. The process includes assessing security controls, policies, and procedures to ensure they meet regulatory requirements and industry best practices. Auditing also helps assess the current security posture and helps identify gaps and weaknesses that must be addressed.
Challenges and solutions
As organizations embrace multi-cloud platforms to manage and monitor their workloads, managing and overseeing these environments can become dauntingly complex. Creating a comprehensive strategy for governance and monitoring that keeps up with changes to the cloud environment over time is often more complicated than believed.
Security compliance
Security compliance outlines an organization's use of cloud resources that aligns with relevant security standards, policies, and regulations.
Compliance requirements could be HIPAA, GDPR, PCI DSS, etc. For example, you’d like to achieve compliance with the Payment Card Industry Data Security Standard (PCI DSS). In that case, it is vital first to understand which cloud services and resources comply with PCI DSS.
Next would be to implement the necessary security controls to meet the requirements of the PCI DSS standard. For example, configuring firewalls, implementing intrusion detection and prevention systems, using multi-factor authentication, encrypting data in transit and at rest, and restricting access to cardholder data.
|
Platform
|
Provisioning Automation |
Security Management |
Cost Management |
Regulatory Compliance |
Powered by Artificial Intelligence |
Native Hybrid Cloud Support
|
|---|---|---|---|---|---|---|
|
Azure Native Tools |
✔
|
✔
|
✔
|
|||
|
CoreStack
|
✔
|
✔
|
✔
|
✔
|
✔
|
✔
|
Conclusion
The public cloud has become the go-to solution for organizations that want to scale their IT infrastructure while minimizing capital expenditures rapidly. While the benefits of the public cloud are clear, security concerns have become a significant issue for organizations. Public cloud environments require careful security governance to protect sensitive data and systems from unauthorized access and breaches.
Corestack's NextGen Cloud governance solution offers organizations a holistic experience by providing unified dashboards to monitor and manage workloads across different hyperscalers. In addition, it provides organizations with a single view into their entire cloud infrastructure and critical insights into workloads and potential security threats. With automated policy enforcement and compliance reporting, CoreStack helps your cloud security governance remain efficient and compliant, even as you scale.